CACHEBOX supports all the common deployment methods for Forward caches. We can help you choose the best one for your network.
Transparent vs Explicit
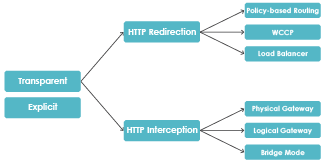 Both explicit and transparent deployments are often used in enterprises.
Both explicit and transparent deployments are often used in enterprises.
In explicit deployments, the user’s client software (usually web browser) is configured to make requests directly via the cache. This entails configuring client devices individually or via a centrally distributed method, e.g. using an Active Directory group policy.
In transparent deployments, client computers do not need to be reconfigured, and web traffic is automatically rerouted via the cache. In this mode, users are not aware of the cache. There are several ways of achieving transparent deployments. They involve either HTTP redirection or HTTP interception.
HTTP Redirection – web traffic is diverted via the cache, while the remaining network traffic remains on its original route. The cache doesn’t need to handle unnecessary traffic so can do more caching.
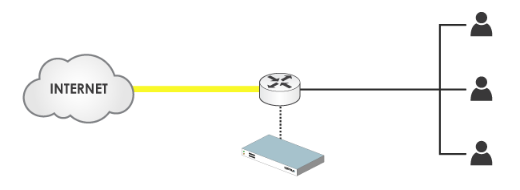
This architecture needs a device which is capable of redirecting HTTP traffic to one or more CACHEBOXes.
Such a device could be:
- A switch, router or firewall which supports Policy-Based Routing or NAT
- A switch or router which supports Cisco’s WCCP protocol
- A load-balancer, when deploying multiple caches
HTTP Interception – all traffic is directed via the cache. HTTP traffic is intercepted and processed by the caching software, while non-HTTP traffic is passed straight through the device.
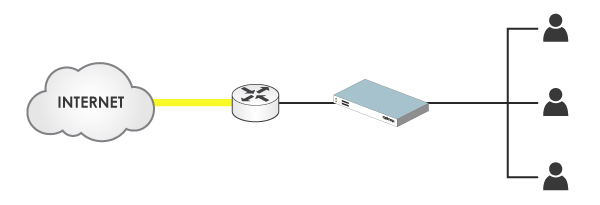
The three possible interception modes are:
- Physical Gateway mode, where the cache is placed directly inline between the router and the network devices. The cache is used as a gateway between two or more subnets and is used as the default gateway by clients.
- Logical Gateway mode, which is similar, but the cache is logically inline rather than physically inline. A switch inline switches all traffic to the cache.
- Bridge mode, where the cache is placed directly inline. Bridged network interfaces on the cache mean it becomes logically a ‘piece of wire’ inserted between the network devices and the router on the same subnet.
With more and more web content moving to HTTPS, many networks benefit from a combination of conventional HTTP caching and HTTPS caching. CACHEBOX offers functionality for intercepting and caching HTTPS traffic for all deployment modes.
Preserve client IPs with Source Address Spoofing
CACHEBOX can mimic the IP address of the client making the requests.
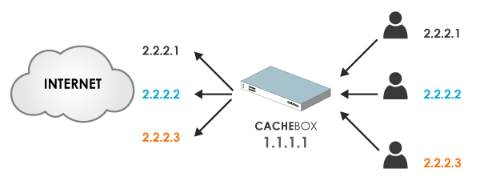
Most caches make requests to web servers using their own IP address. This leads to several problems:
- Many web servers limit the number of simultaneous connections made at one time from a single address.
- If an end user does something illegal online, the IP address of your cache gets recorded in the web server’s logs, not the user’s IP address.
- If your network has a device up-stream of the cache that logs or controls access based on the users IP address then it won’t work as well because it can’t see their IP.
To solve this problem CACHEBOX uses Source Address Spoofing to make requests to web servers using the end user’s IP address.
 Both explicit and transparent deployments are often used in enterprises.
Both explicit and transparent deployments are often used in enterprises.


